Proper storage of Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) is at the core of a healthy and satisfactory compliance program. The issue? There seems to be ample confusion on what CUI and FCI are, the difference between the two, and where they officially can be stored.
Improper storage of both CUI and FCI not only puts your organization’s environment at risk, it also leaves you vulnerable to failing a compliance assessment, contract loss, and heavy fines. We’ve put together this quick guide to ensure you know exactly what is needed and expected of organizations that house FCI and CUI. Keep reading to learn more!
What is the difference between FCI and CUI?
Before we can jump into where CUI and FCI can be stored, it’s important to understand what they are and the differences between them and their protection requirements.
Federal Contract Information (FCI) is information provided by or generated for the government under a contract not intended for public release.
Some examples of this are:
-
- Contract Performance Data
- Project Schedules or Timelines
- Proprietary Proposals or Cost Estimates
- Government-Provided Documents Marked as Not for Public Release
- Work Breakdown Structures (WBS) or Statements of Work (SOW)
- Invoices or Billing Details with Contract Identifies
Protection Requirements come from FAR 52.204-21 and require “Basic Safeguarding.” This “Basic Safeguarding” includes 15 controls to protect FCI.
Controlled Unclassified Information (CUI) is information the government creates, possesses or has disseminated to various DoD contracting companies that requires safeguarding and additional dissemination controls.
Some examples of this are:
-
- Export-Controlled Technical Data (ITAR, EAR)
- Personal Identifiable Information (PII) Involved in a Federal Program
- Defense-Related Engineering Drawings or Specs (Generally CTI)
- Other Categories Found at National Archives CUI Registry
Protection requirements come from DFARS 252.204-7012, 32 CFR Part 170, and the 48 CFR. These reference NIST 800-171 as the framework to be used to protect CUI Data.
What does this Mean for Storing FCI and CUI?
FCI only requires “Basic Safeguarding,” and the 15 controls do not limit where the information is stored. Thus, FCI can be stored on Commercial Cloud Environments, contractor-owned IT systems located on-prem, and encrypted portable devices or media (or unencrypted with proper physical safeguards).
CUI requires more care due to the fact that it is more sensitive and will need more protection. This is specifically called out in DFARS Clause 252.204-7012 Paragraph (b)(2)(ii)(d)
“If the Contractor intends to use an external cloud service provider to store, process, or transmit any covered defense information, the Contractor shall require and ensure that the cloud service provider meets security requirements equivalent to the FedRAMP Moderate baseline…[.]”
Covered Defense Information (CDI) is just another name for Controlled Unclassified Information due to CDI being a category of CUI. This means CUI can be stored on FedRAMP Moderate or High Authorized Cloud Service Providers (CSP), contractor-owned IT systems located on-prem, and encrypted portable devices using FIPS Validated Encryption.
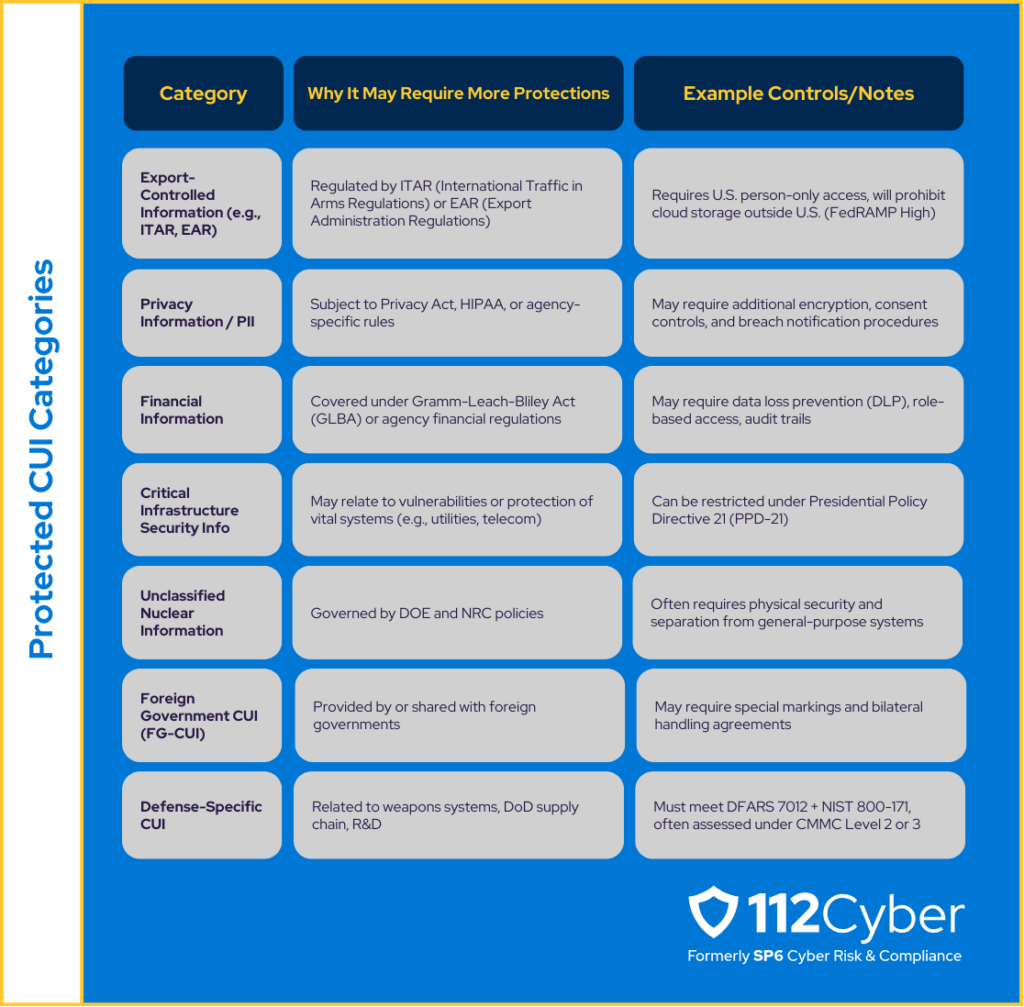
There are some categories of CUI that require increased protection and provide different challenges. The following are some of those categories, but this list isn’t exhaustive, and DoD Specific information will be covered later on in this document:
What Does It Mean When You Have CUI and FCI?
The CMMC Scoping guide has two use cases when FCI and CUI are in the same environment:
Same Scope – If FCI is found within the same scope as CUI then the following applies, “A Level 2 self-assessment or Level 2 certification assessment satisfies the Level 1 self-assessment requirements for the same CMMC Assessment Scope.
If FCI is processed, stored, or transmitted within the same scope as CUI in the Level 2 scope, then the methods to implement the Level 2 security requirements apply towards meeting the Level 1 assessment objectives. The OSA is responsible for ensuring that only authorized users and processes have access to data regardless of its designation.”
Different Scope – If FCI is found in other parts of an environment that is not within the scope of the CUI then the following applies “If FCI and CUI do not share an environment, the two assessments would be conducted independently and methods to implement security requirements in one scope would not apply to the other scope.”
CUI Categories Requiring Additional Security Protections
Export Control (ITAR/EAR) – International Traffic in Arms Regulations (ITAR) and Export Administration Regulations (EAR) requires all data to be processed/stored within U.S. data centers and only accessed by U.S. persons.1
Department of Defense CUI (DoD IL4 or Higher Data) – CUI tied to national defense and military operations generally required U.S. based storage and U.S. personal to access the data.2
Unclassified Controlled Nuclear Information (UCNI) – Regulated by DOE/NRC and has strict U.S. handling requirements of must remaining on U.S. Infrastructure and with U.S. citizen access only.3
Privacy Data with National Security Implications – Not all PII/PHI is U.S.-restricted, but when tied to DoD, IC (Intelligence Community), or federal law enforcement missions, data classification can be upgraded to IL4 or higher. Then the same requirements from the DoD CUI controls apply here.
Why Azure Commercial Is Not Acceptable For This Type Of Data
As we stated before Azure Commercial is FedRAMP High but this does not mean it can handle all data. The categories of data above have two requirements both being U.S. Based and restrict access to U.S. Citizens, and which Azure Commercial does neither.
Wrapping Things Up
Understanding the difference between FCI and CUI is critical to the longevity of your organization’s compliance program. Hopefully the difference between them and how to properly store each is a little clearer after this quick guide. Still not 100% sure or want more information about your environment?
References
122 CFR Parts 120-10 (ITAR) (https://www.ecfr.gov/current/title-22/chapter-I/subchapter-M/part-120)
2DoD Cloud Computing SRG v1r4 (https://www.cyber.mil/dccs/dccs-documents/) – “Access to DoD information at the various levels above level 2 is limited by national affiliation. For other than U.S. citizens or non-citizen U.S. nationals as defined in 8 U.S. Code § 140857, national affiliation is defined in 22 CFR 120.1558 – U.S. person and 120.16 – foreign person.”
310 CFR Part 1017 (DOE UCNI) (https://www.ecfr.gov/current/title-10/chapter-X/part-1017) – “Requirements for routine access. To be eligible for routine access to UCNI, the person must have a need to know the UCNI in order to perform official duties or other Government-authorized activities and must be: (1) A U.S. citizen who is:” (There is a lengthy list of other items on that list but it is all prefaced with U.S. Citizenship)
